USE CASE
Data Entitlement Access Review
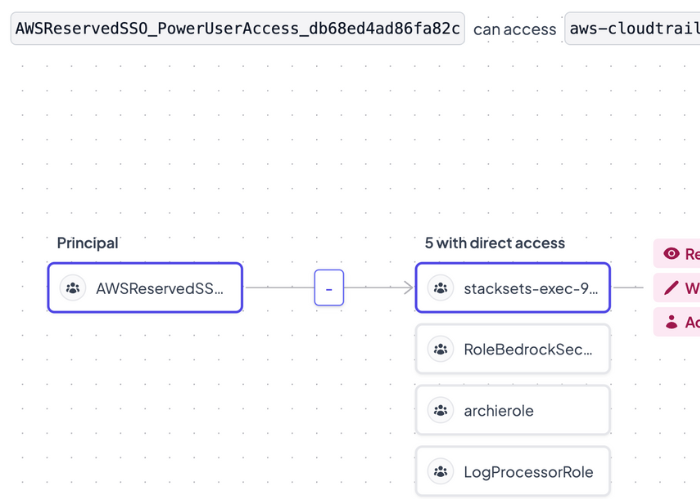
With identities often a key element of data breaches, understanding the full entitlement chain of your identities is crucial for effective risk reduction.
Bedrock delivers next-level visibility into entitlements and access:
- Bedrock automatically charts all identities—human and machine—and prioritizes them by the sensitivity and volume of data they access.
- Our platform tracks the full entitlement chain, discovering permissions that other solutions might miss, such as those involving chains with multiple role assumptions.
- With entitlements mapped, Bedrock identifies critical areas to decrease exposure, like unused sensitive data or expansive permissions, facilitating streamlined, risk-prioritized entitlement reviews.

Our platform brings with it a range of compelling benefits including:
- Complete clarity: Understand your identity landscape for least privilege initiatives.
- Automated discovery: Identify proxy entitlements that have been issued unintentionally.
- Comprehensive scope: Covering both human and non-human identities.
- Unprecedented simplicity: One, unified platform to connect data and identity.